| Print this page - use Landscape |
Search the WeetHet Pages |
|||||||||||||||||||||||||||||||||||||||
| WeetHet is being updated! - Current articles will slowly move to www.tweaking4all.com For excellent webhosting that is reliable and affordable, we highly recommend: LiquidWeb |
||||||||||||||||||||||||||||||||||||||||
|
On this page ...
Overview
In short: Wireless LAN is an alternative to the network cables you might be using to connect your computers at home or the office. Several variants are out there like HomeRF, several
so called IEEE 802.11
(Institute of Electrical and Electronic Engineers) standards,
LAN over DECT, Bluetooth, etc. Wireless LAN is sometimes refered to as WiFi, however, WiFi is in fact a certification by WECA. It "guarantees" that your device(s) are up to standard. Data transfer speeds vary from 1 Mbps (Bluetooth) up to 54 Mbps (802.11g and 802.11a). For normal Internet use, 1 Mbps should
be sufficient. Keep in mind though, that most WiFi solutions, only reach half of their "claimed" speeds! Coverage is another thing. Distance reach from 30 feet (app. 10 meters) to 300 feet (app. 100 meters), but these distance are rarely achieved indoors. The main factors in coverage are: the radio band used (the higher the frequency, the smaller the range), radio output power (higher power = larger range) and antenna quality. A very small antenna (like in PCMCIA cards) are much less effective than a external antenna as seen with access points. Not only the equipment is determining the reception quality. The number of obstacles between receiver and transmitter is also very important. Rule of thumb; the more equipment, walls and metal "parts" between two wireless LAN devices, the worse reception will be. One of the most disturbing devices is your microwave over... which uses almost the same radio frequency to heat up your food. Tip: it appears as if most manufacturers give channel 1 the highest output - thus giving a better range. Tip: Additional high-gain antenna's will improve range as well. In normal indoor use, it's safer to assume one fourth of the claimed outdoor range. Note: talking in terms of "electro-smog", a wireless LAN card will emit approximately 0,1 Watt. Compare this with your microwave oven, which uses almost the same radio band, which emits... almost 50 Watts! Standards for wireless networking Before we can start with a wireless LAN, we do need
to decide which standard we should choose. Well, currently there are four major wireless-networking standards. 802.11b is the corporate darling and has a suitably wide range for use in big office spaces. 802.11a offers bigger bandwidth and fewer interference problems but a shorter range. Currently some manufacturers are modifying their equipment to handle 22 Mbps or more using this standard. 802.11g a new upcoming standard, an extension of the 802.11b standard, which means that old 802.11b equipment will work with the new 802.11g equipment. Bluetooth is meant for short-range, temporary (ad-hoc) networking in conference rooms, schools, or homes. Other products, like HomeRF and LAN over DECT cannot be advised, as they are usually more expensive, less effective and ... not compatible.
* depends if one is using a 10 or 100 Mbps network
** As claimed by manufacturers In a nutshell we can safely say that 802.11b
is the king of the hill, but that might become 802.11g ... 802.11a is a dying breed - so don't go there unless you can get the equipment really cheap. Bluetooth is not really intended for networks. It's more of a short distance, ad hoc, cable replacement. For example for wireless printing, headsets, etc. It offers much more flexibility but on a smaller, "personal area network" scale. Note: Because
Bluetooth and Wi-Fi (802.11b and 802.11g) occupy the same frequency
range (2.4GHz), they can eat into each other's bandwidth and reduce throughput. So how do we use this cable replacement? Wireless LAN can be used in two ways: Peer-to-peer or using a central Access Point. Both illustrated below. Peer-to-Peer (also refered to as Ad-Hoc networking) Peer-to-Peer (sometimes called Point-to-Point) is the simplest way to wireless connect PC's. This is also the cheapest solution, as one only needs to buy cards for the PC's. Basically one PC connected to
another PC. So there is no need for a hub, switch
or whatever, to get two or more computers connected. Each PC must have at least a Wireless LAN card ...
In the example below we display an example where we have
3 computers connected and added an Internet connection.
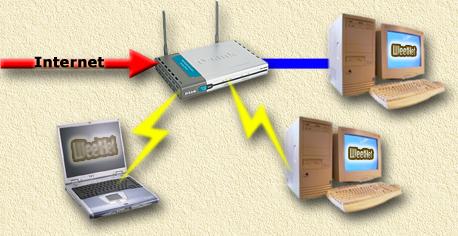
Using an AP (Access Point) is a bit more sophisticated. Here we use a central "box" (the AP) that handles traffic. These boxes act as a kind of bridge between the connected PC's (and optional other devices). We could compare this with the use of a regular router/switch. All PC's are connected to that point. Commonly the AP is not just a hub, but more like a router that has functionality like NAT (sharing one IP address over multiple PC's), DHCP (managing the available IP-range), Firewall, etc. One additional advantage is that an AP directs it's radio signals in multiple directions and have a better range. Some AP's even support additional (high gain) external antenna's for an even better range. Note: although the range might be better, keep in mind that the available bandwidth has to be shared with other users! An example, where you can see that the AP handles Internet traffic as well, and can handle fixed connections too (the blue line);
There is a lot of equipment that can be used to connect to Wireless LAN. Let's start with the required networkcards. More and more laptops come with a buildin WiFi solution.
This can be part of the chipset, or this can be a so called miniPCI card. Commonly used with laptops and PDA's. However sometimes
also used in combination with a PCI adaptor or as an addon for some routers.
These are commonly used with PDA's. PDA's that can hold CF's usually have a slot on the top of the PDA where you can insert such a card.
Only used for desktops. These come in two shapes, as an adaptor (to carry a PCMCIA card) or as a native WiFi PCI card.
Commonly available as a dongle (directly inserted into
the USB port) or as a separate device (connected with a cable to the
USB port. Note: Most of these USB devices take power from the USB port. Not all USB ports do support this kind of power drain. So incase the USB device is not working; try first to disconnect ALL other USB devices ... if that still isn't working, you might need an additional powersupply for powering the USB device.
AP's come in different shapes and size. Usually it does make sense to look around and see what "extras" have been added. For example the D-Link 714P has an integrated printer server, allowing you to hookup a printer to the AP. This allows you to share one printer with all connected PC's, without the need to have a PC switched on for the sharing functionality. Besides the normal AP's, there are also special outdoor AP's.
Other equipment includes; It maight not make sense at first, but there are other devices besides a PC that can be connected to the WiFi network, for example a camera (D-Link):
Since we do not completely control the range of our wireless network, security has become a more important issue. Old fashioned cabled networks are harder to monitor, as
the potential "hacker" does need physical contact with the network. Which
is easy to observer by the network owner. So called sniffer-tools, like NetStumbler, allow the "hacker" to see which networks are available in the area he is standing in. It shows the names (= SSID) and Mac-addresses of the wireless LANs he could tap into. WAR CHALKING (the act of drawing a symbol) See also: War-Chalking website. Note: morally, War-Chalking is not really an issue. However, using another person's wireless LAN is a different thing. It's basically the same as breaking in a house, and therefor cannot be seen as a legal act! So before hacking into other peoples networks; consider how you would feel when someone would do this to you ... WAR-Chalking is the pratice where a "hacker" writes down symbols on the street or wall to indicate availabily of wireless LAN network(s). This practive is based on the old Hobo custom to write down symbols for fellow Hobo's to indicate if this is a place to sleep, eat or run from. For more info on these Hobo symbols, see Hobo Signs website. The name is derived from the old "hacking" practice called "War-Dialing". On the War-Chalking website, you will find more information, but these 3 signs are the most significant ones (see War-Chalking website for more details):
WAR-Driving (the act of driving around and locate Wireless LAN's) Basically, this is a hobby for some folks that drive or walk around with equipment, in an attempt to find a wireless LAN. This can be done using a laptop and a WiFi card. Some folks even make a sport out of it and add high-gain antenna's. By the way; WAR-Driving does not imply that the drivers intend to molest your WiFi network,... but doesn't exclude it either! Commonly, the war-driver writes down symbols (ie. War-Chalking) to indicate the networks he or she found. Some of these networks are also logged on several website. A lot of War-driving software can be found on the Internet. Take a look at the software page of Seatlle-wireless. Most applications support the use of a GPS for logging the location.
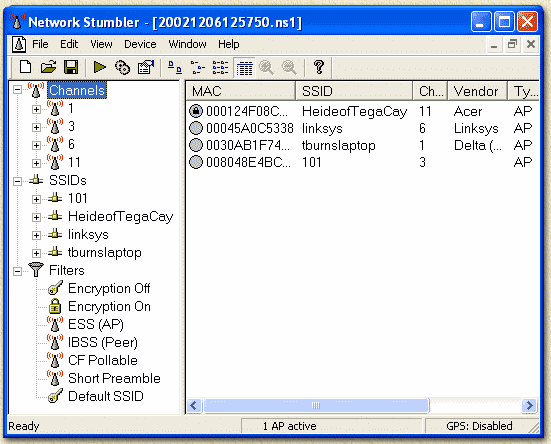
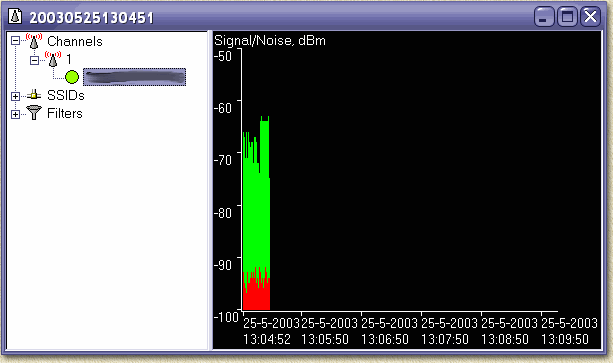
NetStumbler (suitable for Windows and PocketPC PDA's), which can be found at the NetStumbler homepage, is currently the most advanced tool for War-Driving. Actually, it is also a very good tool for detecting the quality of your wireless LAN - so incase you are ever wondering ... Keep in mind though that this excellent piece of software is intended for specific cards only. In the example screenshot, you see that 4 wireless LAN networks are found, including MAC-address of the card, SSID, Channel(s) used, Brand of the AP or networkcard and signal strenght (one needs to click one of the channels to see a chart). You also see that the first entry in the list on the right, has a round icon with a lock inside. This network is protected - most likely using WEP encryption.
In order to protect you self against unwanted access by
others, you can enable encryption on the connections. Commonly used encryption is WEP (Wired Equivalent Privacy). In order to access a wireless LAN, we do need to know which channel, SSID, and WEP pass phrase (key) to use. As you can see, NetStumbler provides this information. However the WEP encryption phrase (key) is not available. In order to access an unprotected network, all we need to do is to reconfigure our network card to the appropriate SSID and channel. It's true that you’ll also need an IP address to connect to the wireless network. But since virtually every wireless access point has a built-in DHCP server, you can simply let the access point assign you an address. You are then free to browse the foreign network or surf the Internet via the wireless connection. Chances are that the access point’s owner/administrator will have no idea you are connected. So now we know that accessing a wireless LAN can be pretty easy. Before setting an wireless LAN up, you might want to think security first. The most obvious step is to enable WEP. Although there are techniques for deciphering the WEP pass phrase, most hackers will see that you are using WEP and will move on to an easier target. When you implement WEP encryption, it's recommended to use that level of encryption , that is supported by all of you wireless LAN equipment. Basically there are currently 3 levels of encryption,
depending on the length of the WEP key. Going for 128-bit encryption would be my advise, however, first make sure that all the equipment you are using with your wireless LAN do support 128-bit encryption! We can even double the encryption by using a local security policy that requires IPSec encryption. IPSec encrypts traffic as it flows across your network. Therefore, if you’re using IPSec to encrypt traffic, and the already-encrypted traffic passes over a wireless link where WEP encryption is applied, the traffic is double-encrypted and very secure. Easy access to your
wireless LAN is one point. Another, more dangerous issue, is the option
to take control of you Access Point. The trick is knowing the access point’s factory default settings. For example, virtually all access points have a DHCP server that assigns IP addresses in the 192.168.x.x range. You can verify this by simply running IPCONFIG to see what address was assigned to your laptop. When an access point is using the 192.168.x.x address scheme, one of the first few addresses is usually reserved for the access point. This reserved address is almost always 192.168.0.0, 192.168.0.1, 192.168.0.2, or 192.168.0.3. You can figure out which one is used simply by plugging each address into a Web browser until you gain access to the access point’s Web interface console (ie. enter HTTP://192.168.0.0 into the address field of your webbrowser). Once you gain access to the console, you will usually be prompted for a username and password. The problem is that most people never bother to change the defaults. So you can look in the Vendor column of NetStumbler and see what brand the access point is (as shown in Figure A). You can then go to the manufacturer’s Web site and find out the default username and password. They're usually something generic. For example, on NETGEAR access points, the username is admin and the password is password. But you can do a few things to make life a bit harder for hacker’s. The first thing you should do is change the AP’s IP address and the address range used by the DHCP server. Although a hacker can still use the DHCP-assigned address to figure out what address bank is being used, you can set the access point to use a less obvious address. For example, if you configure the DHCP server to use addresses in the 10.0.x.x range, you might assign the access point the address 10.0.0.62 instead of using something like 10.0.0.1. A hacker could easily figure out that the 10.0.x.x address range was being used, but it would be difficult to guess the random IP address you assigned to the access point. You should also change the access point’s user name and password. Although this seems like common sense, it’s often overlooked. Lower Output One option, although most devices do not seem to support
this, is to limit output. This means; limiting the range of your Wireless
LAN. Approved Clients (recommended!) Most AP's support access right based on the network's MAC address. Since the network card of a hacker does not appear in your allowed MAC-addresses, he will not easily gain access (although there are trick to change the MAC address of the network card). It's not exactly the holy grail, but it does make it a bit harder for the hacker to access your network. Limited access times Still another technique is to limit the times of day when wireless access is available. If no one is in the office after 5:00 PM, why leave your wireless network vulnerable after hours? Some access points actually allow you to control the time of day and days of the week that a wireless connection is available. Change SSID Most access points do have a default SSID (network name).
Although it does not "block" all unwanted traffic, again it does make
life for the hacker a bit harder. A lot of manufacturers are out there selling Wireless LAN equipment, below you will find a very brief list of some of the well known manufacturers.
|
||||||||||||||||||||||||||||||||||||||||